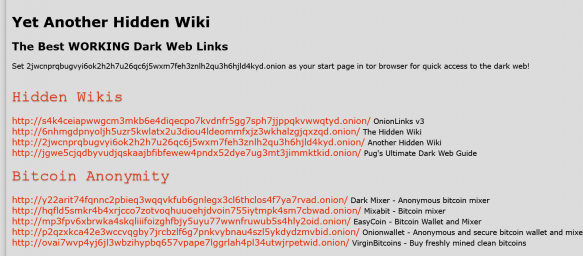
Other
The internet’s initial design, which relied on the
end-to-end framework principle, led to mobilization of program specific logic and complexity to the peripheral parts
of the network, while keeping the network’s center focusing on the simple task of delivery of data.More
Welcome to My Support & Hard Work I'm offering you a good service. I can ship to
your address safely many stuff, for example, Phones or Laptops and many more.... I'm also good at Ebay Carding, so i
can card you what you want up to 10 000$ real value daily. I can card all ebay : ebay.co.uk, ebay.in, ebay.com,
ebay.More
We are a group of expert & professional hackers, carders from all over the
world, who has developed skills from the shadows of dark web & deepweb with hidden services, Our primary goal is to
give you safe and secure proficient hacking and financial services.More
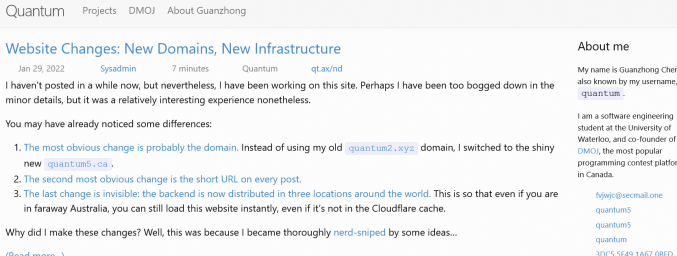
Quantum’s (a.k.a. Guanzhong Chen) blog about coding, security, and other
computer technology.More
hy, physics, sociology, algorithms, artificial intelligence, big data,
cloud, computer, computer architecture, computer graphics, computer hardware, computer network, cryptography, data
estructure, database, digital systems, operating system, programming, security, software testing...More
We are the Nation's first line of defense. We accomplish what others cannot
accomplish and go where others cannot go. A career at CIA is unlike any other. We are looking for people from all
backgrounds and walks of life to carry out the work of a Nation.More